Five fundamental ways to reduce cyber risk by 70 percent
Oct. 22, 2018
This paid piece is sponsored by Eide Bailly LLP.
By Eric Pulse, Eide Bailly director risk advisory, CISA, CISM, CRISC, GSEC, CFSA
“No, not me,” you say. “I don’t have any reason to be concerned about cyber risks. That happens only to big corporations in large metropolitan areas.”
The truth is hackers know no bounds, have no “minimums” and target business large and small. And cyber thieves are at work right here in our back yard. We frequently receive calls from Sioux Falls organizations who have discovered breaches — from the employee who unwittingly sent sensitive data to a spoofed address to the employee who responded to a crafty phishing scam — and are frantically trying to assess the damage. These innocent mistakes can put your company’s survival on the line.
October is Cybersecurity Awareness Month. So we thought this would be an appropriate time to share our white paper “The Fundamental 5 Ways to Reduce Cyber Risk by 70 percent.” Read on.
Executive summary
There are some very important executive decisions that drive good cybersecurity hygiene in well-run, well-protected companies.
It is not to say that well-run companies do not get breached, but all indicators lead to the conclusion that if certain things are done from the top down, the effects and cost of defending your company against data breaches and recovering from a breach can be reduced substantially.
Survivability of the company is at stake. Could you survive having all operations shut down, fearful customers, unknowns that may never be known and millions of dollars of profits spent on operating without incoming revenue? It is a reality and directly related to leadership, execution and sustainability of key cybersecurity practices and controls.
It is the executive function to ensure these practices are achieved sufficiently to ensure the survival and profitability of the company. This white paper lays out the “Fundamental 5” ways executives can dispatch this duty and potentially reduce those risks by up to 70 percent.
“What the heck is happening?” Root causes of data breaches
If you’re thinking that just the “big companies” get hit by data breaches — you are in a word, WRONG.
If you think that, as a business leader, you are powerless — you are WRONG. In fact, if you are a C-level executive, 53 percent of the root causes of breaches are within your control.
According to the authoritative IBM-sponsored 2017 Ponemon Institute’s Cost of Breach Report:
- 28 percent of all breaches involved system glitches, including both IT and business process failures, which are operational factors that are preventable.
- 25 percent were human-factor errors by negligent employees or contractors, which are also largely preventable.
- The other 47 percent involved a malicious or criminal attack, which is what most of the hype is about in the press.
The Ponemon study also reports that the average number of records in a U.S. breach is 25,802 and the cost of remedy in the U.S. for each of them averages $225 per data record. That calculates to over $5.8 million from your bottom line “not if, but when” your company is breached.
“What ARE you doing?” Corporate leaders should lead the fight
Many corporate leaders outside the IT group have incomplete information, not only about what is actually happening with cybersecurity controls, including the allied programs and related projects. It is not to say that there have not been briefings, reports and information. But sometimes the acronyms and bits and bytes get overwhelming or even seem irrelevant. Because new data breaches are happening daily and being reported on in the media, two things tend to happen. First, you may become desensitized and begin to not listen closely. Or, conversely, you could become hyper-focused on a new threat category such as a new offending malware. Neither one of those reactions really accomplishes the best outcomes. So what to do?
Based on the 2018 Verizon Data Breach Investigation Report as well as some insights of over 15 years of cybersecurity hygiene interpretation, this white paper will give you a different view of what envelops this cyber hygiene view. In its 11th edition of the annual report, Verizon has actually done a fine job by inserting humor, satire, movie references and quips to make the reading more fun, but with all of the acronyms, graphs and phraseology, the bad news is still there, which can make it a daunting challenge to understand and get through.
“I am convinced that there are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again.”
Robert Mueller, former director of the FBI: 2012 RSA Cyber Security Conference
Cyber hygiene is a reference to the steps individuals and companies can take to maintain system health and improve online security. Like personal hygiene, these practices should be made routine to ensure the safety of data that could be stolen or corrupted and to defend against common threats.
A very strong case should be made for a top-down cyber hygiene program, which if done correctly by following some best practices, companies can reduce up to 70 percent of cyber risk.
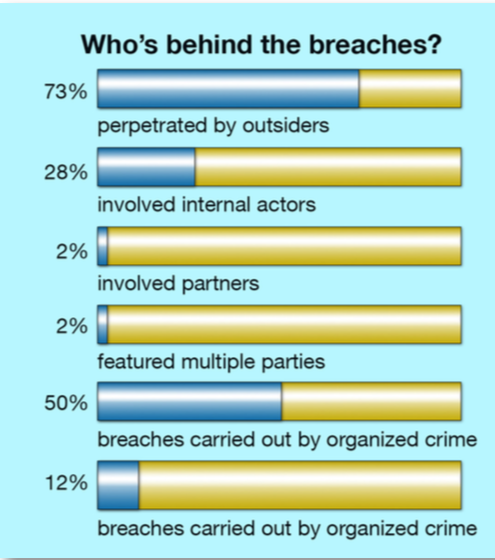
Based on your company, only you can know what the priorities for concern are for sure. Regarding the overall view of the cyber landscape, the Verizon report states: “Most of the data breaches are caused by outsiders, but surprisingly almost a third of them involved internal actors (employees or contractors). Organized criminal groups caused a stunning 50 percent of the breaches whereas nation-state (China, Russia, North Korea…) sponsored activity is lower in volume.”
Based on Verizon, Ponemon, the cyber world and the analysis of the facts, below are the “Fundamental 5” areas where executives should focus first to reduce the risk target that is on their company:
- Top-down approach
Having a complete view of the business plan and balancing priorities is clearly a C-suite responsibility. Determination of a security framework and governance process must be clearly thought out, planned out and worked out from the top for consistency’s sake and to align with the company’s true business risks. It is said that another name for the “bottom-up approach” is rebellion.
Determining, building and supporting a corporate culture takes time and effort. People follow clarity. That clarity comes from the top to establish a corporate culture. All industry reports show that a culture where everyone is responsible for information security, at whatever level, brings the highest rates of return.
It stands to reason that the faster a data breach is uncovered and contained, the less it will cost, but most organizations still have a lot to do in this area. If you use these “Foundational Five,” then you are as ready as can be expected. Ponemon found the average time to identify was 191 days last year, with an additional 66 days on average required to contain the breach. These times could be reduced if every organization would keep up to date with NIST’s Cybersecurity Framework and keep tighter control of its data.
- Guard against social attacks
Mostly done via email or phone but other means are used to retrieve information that can be used to capture and collate information, so reconnaissance can be done. Two types are called out and represent 98 percent of social incidents and 93 percent of breaches. Phishing is most commonly a precursor followed by another action by a perpetrator.
- Phishing is used to influence the recipient to click on something that will compromise their credentials or give up information the perpetrator can use in a subsequent effort.
- Pretexting is similar to phishing, but the perpetrator uses a two-way dialog and impersonation of a person of authority to get the recipient to do something. A prevalent example is a request by an executive to someone in HR to send I-9 information or to wire transfer funds immediately to a third party.
- Email is still the most common method — 96 percent — of compromise.
What you can do about social attacks:
- Remember that your credentials to your systems are valuable and the primary reason for the attack. If they can look like you, they can go unnoticed in the system. They use your identity to spend months and years searching for whatever they want to steal, and they look like they are supposed to be there. They look like you!
- Put policies in place so employees and contractors know what is expected of them — especially in financial, HR and IT roles. Those are the “soft targets” with important data.
- Require a review and acceptance of responsibility to those policies in employment agreements and third-party contracts.
- Establish a corporate culture from the top that everyone complies with security policies.
- Establish an employee and third-party awareness program, so everyone knows it is everyone’s job to be secure.
- Utilize software that hardens your email system from unwanted and known malicious sources.
- Beware of ransomware
As the Verizon DBIR reports, ransomware has overtaken all other malware to be the most prevalent variety of malicious code for this year’s dataset. Ransomware locks up or encrypts your data or systems, or both, so the perpetrator can exact a ransom amount for its safe return. The worst part about this menace is that it is:
- Used opportunistically against everything from individuals’ home computers all the way to targeted large scale attacks on corporate and governmental systems.
- Relatively inexpensive to launch against a target, giving a low risk-to-return ratio.
- Highly successful and easy to disappear into the internet.
- Fairly difficult to catch perpetrators, recover ransomed data or recover funds.
What you can do about ransomware:
- Make sure your data and operating systems are regularly backed up and segregated into offline storage. If the attacker can’t get it, and you can restore it easily, there is no motive to pay them. Frequency of backup depends on the amount of data you produce and its value to you and your clients, determining what data you can afford to lose and what you cannot, and the technology you have available to you.
- Segment your data into logical groups by type and role of those who need the data. It makes you a smaller and less profitable target.
- Think about business continuity and how you want your company to be positioned after the crisis is past.
- Provide security training
In the social attacks section above, awareness is a good start to getting your people to understand they have a responsibility to protect their identity and credentials. This addresses the “why and who.” Now complete their capabilities with a focus on the “what, where and when.”
- All company staff members should be capable of recognizing basic attack indicators, including phishing emails, URL abnormalities, unusual system activity and even an unexpected call from IT asking about credentials.
- Provide employees and contractors with a very quick and easy way to report social attacks and encourage them to do so. Provide a link to security where they can immediately forward suspicious email and communications for review by a professional.
- Establish an environment where there is an expectation of no privacy on company computers, servers, networks or internet connections. Numerous studies conclude that where there is no expectation of privacy, user behavior improves.
- Have routine security audits to continually verify processes are being followed. Many companies reward good behavior by employees with incentives and recognition.
- Ensure basic antivirus is installed AND up to date
Although the Verizon report does not have specific statistics, it does note, “As evidenced by the great number of ‘integrity’ issues in our caseload, many breaches continue to involve assets without basic antivirus protection installed” — hence the addition of “up to date.” Most new computers come with an antivirus package installed. However, when the year license runs out, many are not renewed or the updates get turned off because they “impact performance.”
- Require by security policy that antivirus/malware that meets a declared standard is installed and operational at all times, on all personal computers and other devices that connect to company networks.
Additional IT-based approaches that may fit your company
The “Fundamental 5” areas to focus on first will help reduce risk overall. The challenge is that there is no solution or approach that can bring 100 percent security; however, the following are actions and policies that the IT team should implement:
Software patching and out-of-date equipment
This is another area of keeping “up to date.” Because of the rapid evolution of hardware and software, capability obsolescence and going out of manufacturer’s support can be, and often is, deadly to your data. If you are running a computer on the Microsoft XP operating system, you are putting out a sign “Come Steal from Me” on the Internet. It is happening every day around the world.
- If you must use out-of-date equipment, use it where the data is not proprietary and/or does not connect to your network.
- Work to assure patching of software is done in a timely way. Sometimes immediately is not feasible. Patching is the way of keeping new threats from hitting the software’s vulnerabilities. It is a cat-and-mouse game with hackers. Don’t be the mouse they eat.
Multifactor authentication
This is the realization that in today’s world passwords are highly ineffectual for most people. IT staff or “privileged users” — those who routinely access data that is classified as something other than standard or public use — have a real requirement to move into two-factor or multifactor authentication. It requires a higher standard of proof that the person entering the system really is who they say they are.
- Two-factor or multifactor authentication for only specific users is less costly and greatly reduces risk. If it can be done for all employees, then it is that much better
System segmentation
By having laptops, desktops, smart devices and printers connecting directly to the servers that provide the data to them, you’re giving attackers the direct shot they’re looking for. Dividing a network into subnetworks is smart for several reasons:
- The security of information that someone on one subnet cannot go directly to another subnet provides data control. Not allowing manufacturing open access to HR data is a good segmentation.
- Traffic efficiency and increased speed of transactions on a system of subnets is a benefit everyone really likes.
- It is easier to monitor traffic on a set of subnets and see anomalies of bad traffic or threats.
- Use the information security principle of “least privilege” where people only have access to the data they require for their jobs. That is all they get.
Device and data security
- Full disk encryption is both an effective and low-cost method of keeping sensitive data out of the hands of criminals. Even if it is misappropriated, the ability to unencrypt it without the proper keys makes the data worthless. It comes as a part of most computer operating systems and simply needs to be turned on.
- Data loss prevention tools provide controls to identify and block transfers of data from your networks onto a thumb drive or out through someone’s personal email account.
“When you get hacked or breached, then what?” Implement an incident recovery plan to survive the attack
As stated above, there are certain, and not always costly, things you can do to significantly reduce your risk profile, as well as the craziness and costs in the event of a breach of your data.
We all should embrace the fact that the number of breaches in the world will increase every year, thus making the probability of your company being victimized an increasing possibility. Reducing the impact, cost and even the chance of overall business failure is in your hands. Embracing a corporate culture that data privacy and security is everyone’s responsibility and key core values as mentioned above is critical to success.
Having an incident recovery plan as directed by the C-suite is a defining step to reduce cost and effect of a breach.
- Define the roles and functions in advance of a breach for the incident response team.
- Ensure that your CIO or CISO, legal, marketing, public relations and incident response manager at a minimum are all part of your incident response team.
- Determine if you will have an internal or a hired incident response manager. It is not a position to be filled with someone with little or no current breach experience.
- Determine if you are going to have cyber liability/cyber breach insurance. The more prepared you are the less the insurance will cost. It looks small in comparison to what you will spend to recover on your own – or the cost of going out of business.
- Have your attorney briefed and in place as well as your insurance broker.
- Have a written definition of an “event” and a “breach,” so you know when you actually need to push the “breach” button. This will help you avoid a very costly error by pushing when it is not a breach.
- Have an idea of who you are going to call and when they need to be notified.
- Perform self-evaluation and eventual outside evaluation of your readiness plan and execution.
- Practice the plan multiple times in a tabletop exercise. Go through the steps and refine as situations change.
- Gather an understanding of what caused the breach.
Your incident response manager will guide you through the incident and ensure that all steps necessary to reduce risk of litigation are taken. The point of forensics is to spend the time investigating the technical aspects of the breach to identify how the breach occurred and what actually happened as a result of the breach. How did they get in? What systems did they access? Did they exfiltrate any data? How do we clean this up? Answers to these questions will then be passed to the incident response manager to work with C-level executives, the attorney and other team members to make further decisions. Ultimately, the goal is to find out if the breach requires notifications and what needs to be done to mitigate further risk.
Have a response plan in place to save about a half-million dollars, maybe more
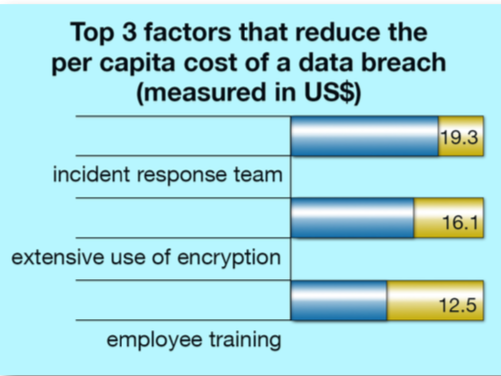
The Ponemon report showed that if a company has an incident response plan and it includes an incident response team already designated, it can reduce the cost of a breach by up to $19 per record. So that calculates with the average number of records in a U.S. breach being 25,802 to $490,238. That’s a good motivation to be prepared for “not if, but when.”
Looking for additional information on cybersecurity? We know you’re busy, so our collection of cybersecurity articles have you, the executive, in mind.
Download our free eBook—access it here anytime. Interested in speaking to one of our cybersecurity professionals? Contact Jessica Armstrong at [email protected] or 605.339.1999.